Microsoft OAuth
Creating a custom Microsoft OAuth application
Step-by-step instructions below closely follow Microsoft documentation to create a new application for ngrok within the Azure portal.
Register an application
- Sign-in to the Azure portal then select or create a tenant for your application.
- Search for "Azure Active Directory" and select it.
- Select "App registrations" on the left hand navigation.
- Select "New registration" at the top.
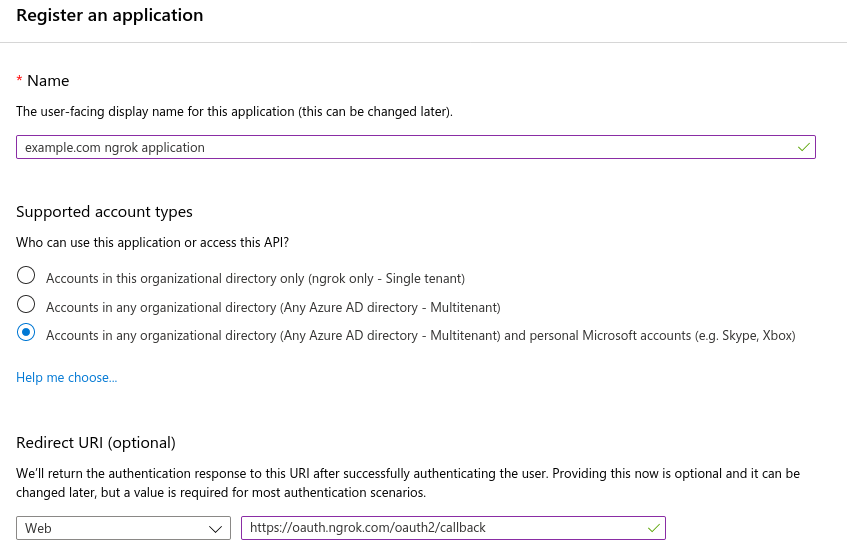
- Enter a name for your application.
- ngrok does not support single tenant applications. Choose supported account types from:
- Accounts in any organizational directory (Any Azure AD directory - Multitenant)
- Accounts in any organizational directory (Any Azure AD directory - Multitenant) and personal Microsoft accounts (e.g. Skype, Xbox)
- Choose a "Web" redirect URI and enter
https://idp.ngrok.com/oauth2/callback. - Register your application. The final form should resemble:
Configure your application
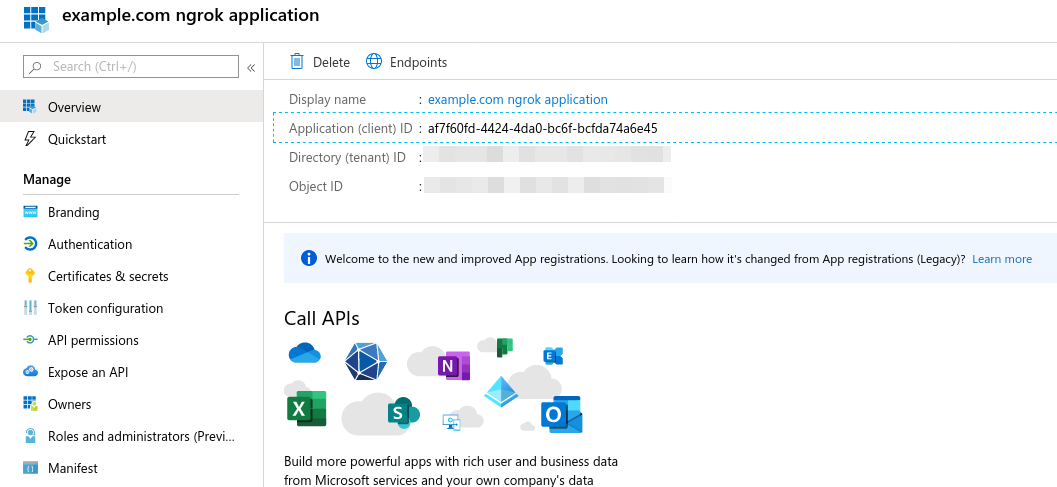
- When viewing your application, choose "Overview" on the left hand navigation.
- Store the "Application (client) ID" in the top information section for later.
- Select "API permissions" on the left hand navigation.
- Add additional scopes that your application requires and store them for later.
- Scopes which require an application review by Microsoft are unsupported.
- Scopes that require admin consent prevent tenants' users from authorizing until consent is granted.
- Ensure
User.Reador a more permissive scope (e.g.User.Read.All) is configured for ngrok. Example minimal configuration: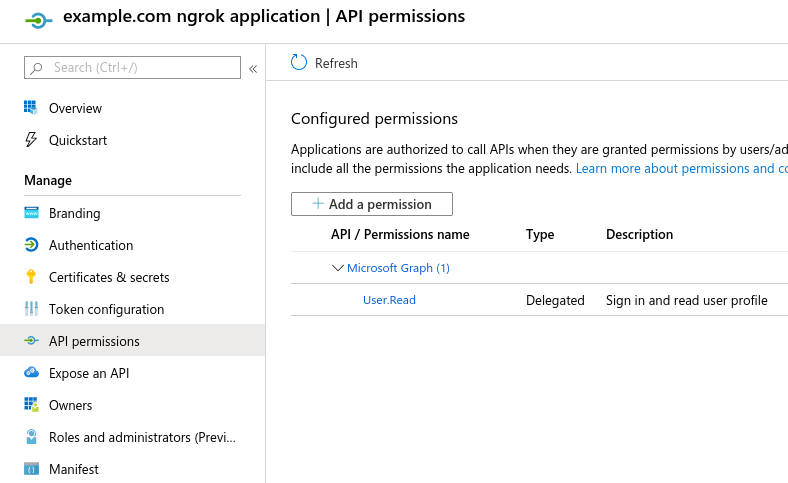
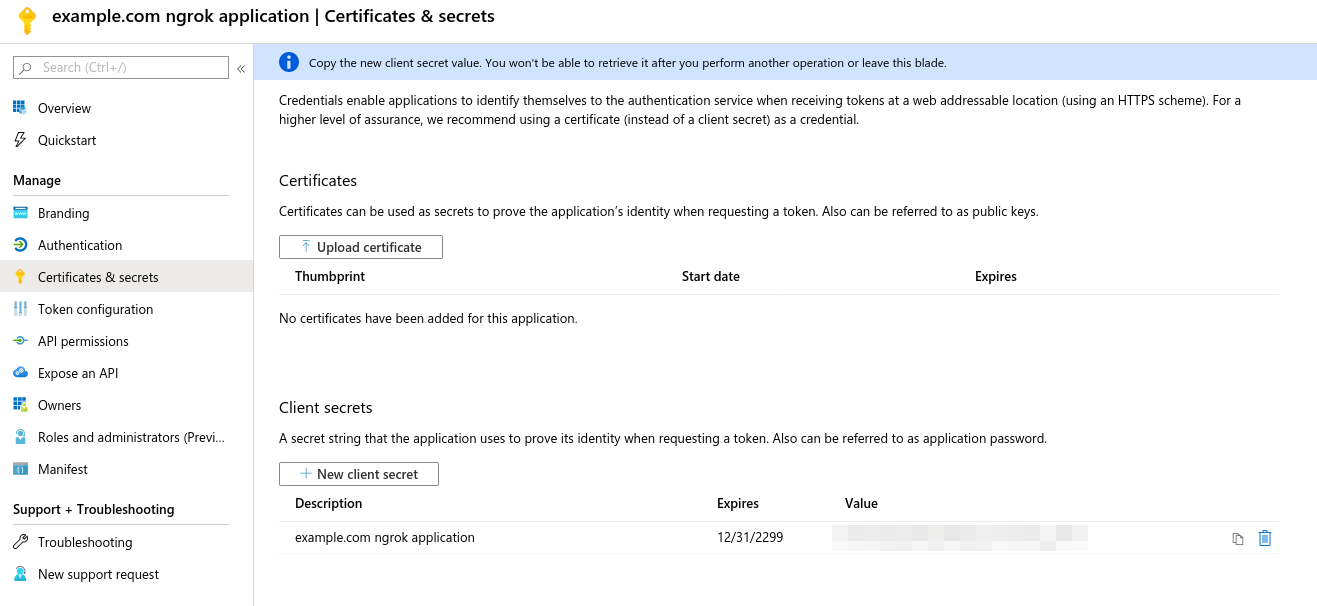
- Choose "Certificates and Secrets" on the left hand navigation.
- Select "New Client Secret" at the bottom, name the secret, set an expiration, and hit create.
- Creation is asynchronous. When complete, save the secret from the "Value" column (blurred below) for later:
Update your endpoint configuration
- Return to the ngrok dashboard and create or edit an OAuth endpoint configuration module.
- Choose to use your own application with Microsoft as the provider.
- Include the scopes, client ID, and client secret for your application.
Additional application setup information
- Creating an Azure AD tenant
- Permissions and consent (restricted permissions)
- Graph API User object properties (id, displayName, and mail/userPrincipalName)